Other content in this Stream
 28:36
28:36All Your Data Я Belong to You: Utilizing the HackerOne API to Power ML/AI and Custom Analytics
 30:24
30:24Strengthen Your Security Posture with a Continuous Cycle of Vulnerability Intelligence— with Hyatt Hotels and DoD’s Defense Cyber Crime
 14:29
14:29Build Resistance to Attacks by Unlocking the Value of Ethical Hackers - Gartner Speaking Session
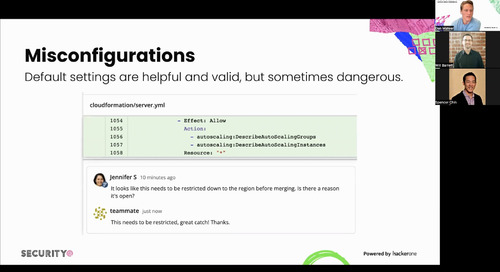
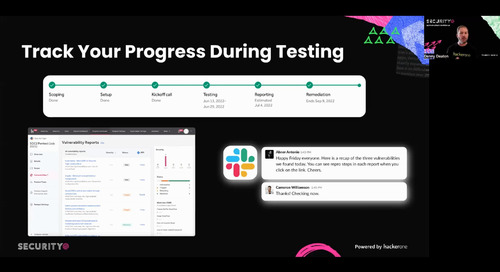
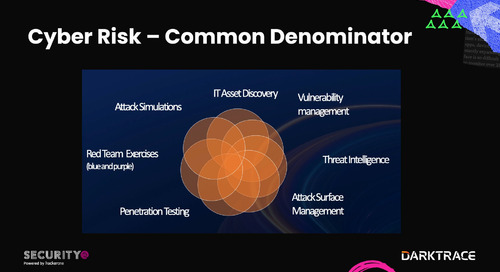
HackerOne Announces Agenda for Fifth-Annual Security@ Conference
HackerOne Announces Agenda for Fifth-Annual Security@ Conference alice@hackerone.com Wed, 08/25/2021 - 05:50 Read more about HackerOne Announces Agenda for Fifth-Annual Security@ ConferenceAugust...