Secure your codebase with human-led audits
Automated scans for assessing at scale, human experts for assessing in-depth. Code Security Audit ensures nothing slips through the cracks.
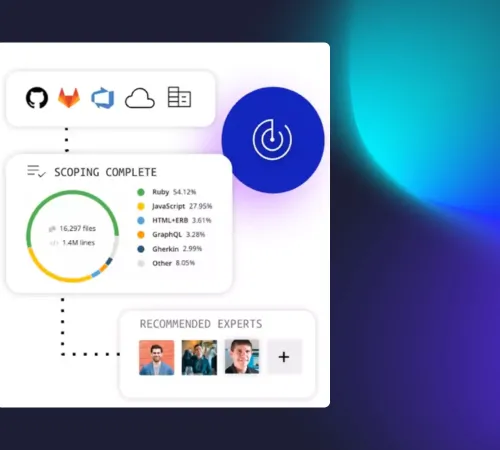
Scoping and setup
The process begins by setting up secure access to your source code repositories hosted on premises and platforms such as GitHub, GitLab, Azure DevOps, and Bitbucket. A dedicated member of your HackerOne team confirms the scope and ensures the code is prepared for review.
Codebase analysis and preparation
HackerOne sources the most qualified reviewers from our network of 600+ vetted experts based on your specific codebase and requirements. The reviewers use best-in-class repository scanning tools to build a contextual understanding of your code.
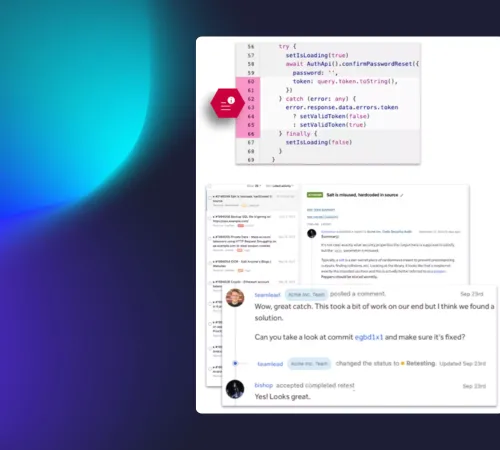
Human-led and automation-assisted review of code at scale
Automated coverage includes software composition analysis (SCA), static application security testing (SAST), infrastructure as code (IaC) scanning, and secrets detection.
Experts review these automated processes to identify critical focus areas and delve deeply into novel issues within large codebases. Manual code review, adhering closely to the OWASP Code Review Guide, uncovers multifaceted vulnerabilities and design flaws that automated tools may miss.
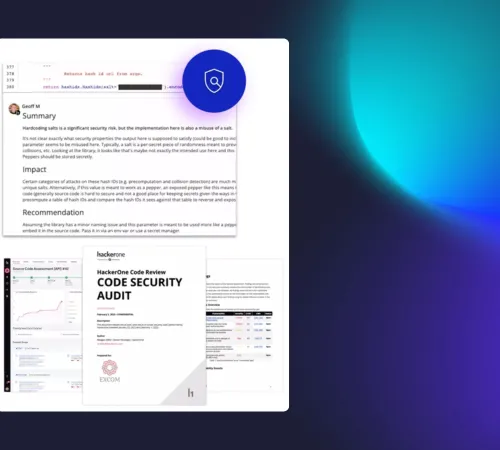
Reporting and remediation
You receive a detailed PDF report outlining identified vulnerabilities, their severity, and actional remediation guidance. HackerOne also facilitates the review of code changes to validate mitigation.
For executives & auditors
Wondering what a final Code Security Audit report looks like?
For software architects & developers
Our findings are contextually delivered inline with your tools for optimal context and collaboration.