Cut through the noise to resolve vulnerabilities faster.
Our Triage team is available 24/7 to validate vulnerabilities, prioritize risks, and streamline remediation.
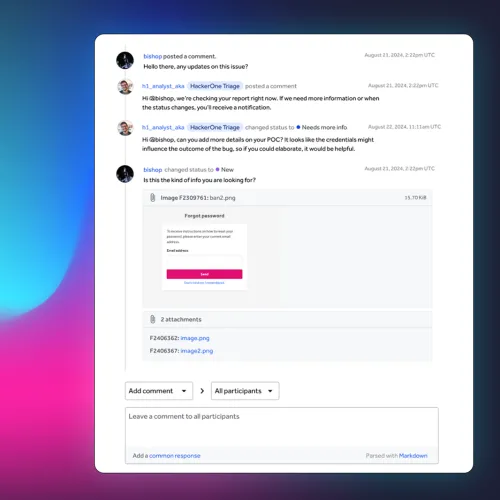
Submission and initial review
Security researchers submit vulnerabilities to your HackerOne program for analysis.
- Triage experts organize and prioritize reports to ensure no submission is overlooked.
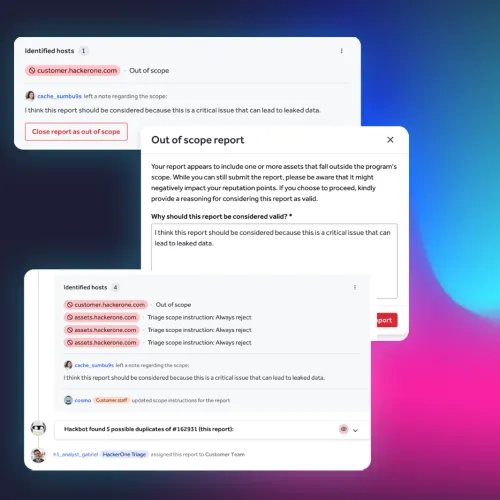
- Duplicate or out-of-scope reports are filtered out based on available information to save your team time.
- Reports with incomplete information are sent back to security researchers for more details.
- All submissions and statuses are viewable in your inbox.
Validation and reproduction
Our security analysts verify the legitimacy of each report and reproduce the vulnerabilities.
- Detailed reproduction steps help your team quickly address issues.
- False positives are removed, focusing attention on vulnerabilities with tangible impact.
- Real-time engagement with your team is needed to ensure sufficient internal context is gathered before making decisions wherever necessary.
- Key insights make remediation as seamless as possible.
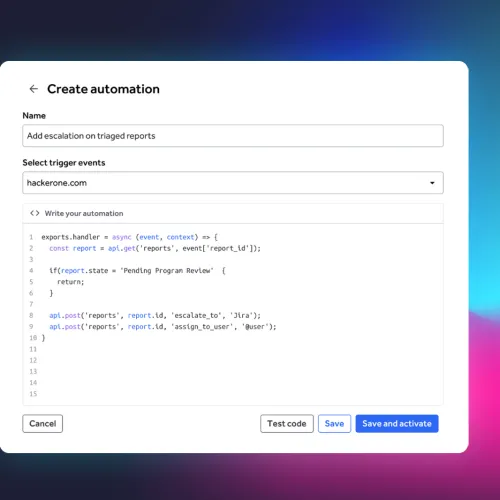
Delivery of actionable reports
Final reports are clear, actionable, and fit seamlessly into your workflow.
- Summaries highlight vulnerabilities, severity, impact, and remediation steps.
- Optional customized formats align with your development processes for ease of use.
- We gather feedback to continuously improve your delivery experience.
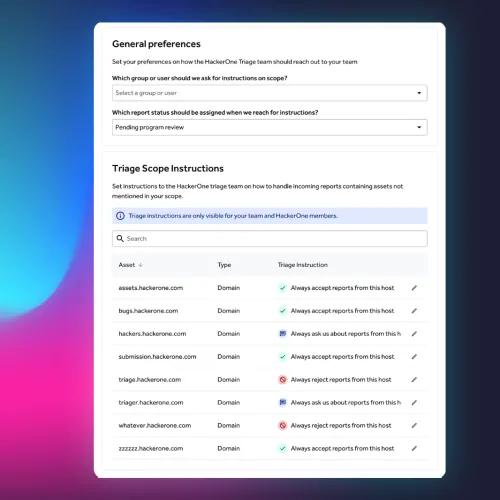
Hacker communication and mediation
We manage ongoing interactions with researchers for smooth communication.
- Our experts clarify details to prevent disagreements with hackers.
- Critical communication issues are escalated directly to your security team.
- Mutual respect fosters engagement and protects your brand.
Frequently asked questions
Outsourcing triage ensures that only validated high-priority vulnerabilities reach your team, saving time and resources. With HackerOne, you gain access to a team of experienced analysts, reducing noise from false positives and duplicates while accelerating vulnerability resolution. This allows your internal team to focus on remediation instead of manual report validation.
Once a hacker submits a report, a HackerOne analyst acknowledges receipt and begins reviewing the report for scope, duplicates, and context. If needed, the analyst may request additional information from the hacker or the customer. Once the report is clear, the analyst validates the vulnerability by reproducing it and writing a detailed summary, including steps to reproduce it, and a severity rating. The validated report is then sent to the customer for further action. After validation, the customer can ask follow-up questions, which the analyst will address within response time goals.
The HackerOne Triage team consists of highly skilled analysts with expertise in vulnerability assessment and deep familiarity with the ethical hacking community. Every report is carefully reviewed, reproduced, and ranked by severity to ensure that only actionable issues are escalated. Continuous training and direct feedback loops with customers maintain high-quality standards.
During onboarding, we establish program goals, review your workflows, and set up communication channels with analysts on your program. We distribute necessary credentials and ensure understanding of assets and scope. We work collaboratively to understand your vulnerability handling preferences, ensuring seamless integration with your processes. The onboarding process typically takes a few weeks and is fully guided by our customer success team.
Our triage service offers tiered packages to suit your program’s size and needs. Some tiers allow customizations, such as defining vulnerability handling instructions, escalation processes, and preferred communication methods. These options and customizations ensure that triage aligns perfectly with your team's workflow and security objectives.
Triage services help you meet compliance requirements by ensuring critical vulnerabilities are identified, validated, and resolved quickly. Our process is aligned with common security frameworks, providing detailed reports and audit–ready data to support your risk management initiatives.
HackerOne’s analysts act as intermediaries between your team and researchers, fostering transparent and respectful communication. This includes clarifying report details, resolving disputes promptly, ensuring hackers feel valued, and strengthening program engagement and trust in your brand.
Our experienced analysts handle all research or communications, clarifying report details and mediating disputes on your behalf. If necessary, critical issues are escalated directly to your team for resolution, ensuring smooth collaboration and maintaining positive relationships with the researchers.