Continuous Vulnerability Discovery
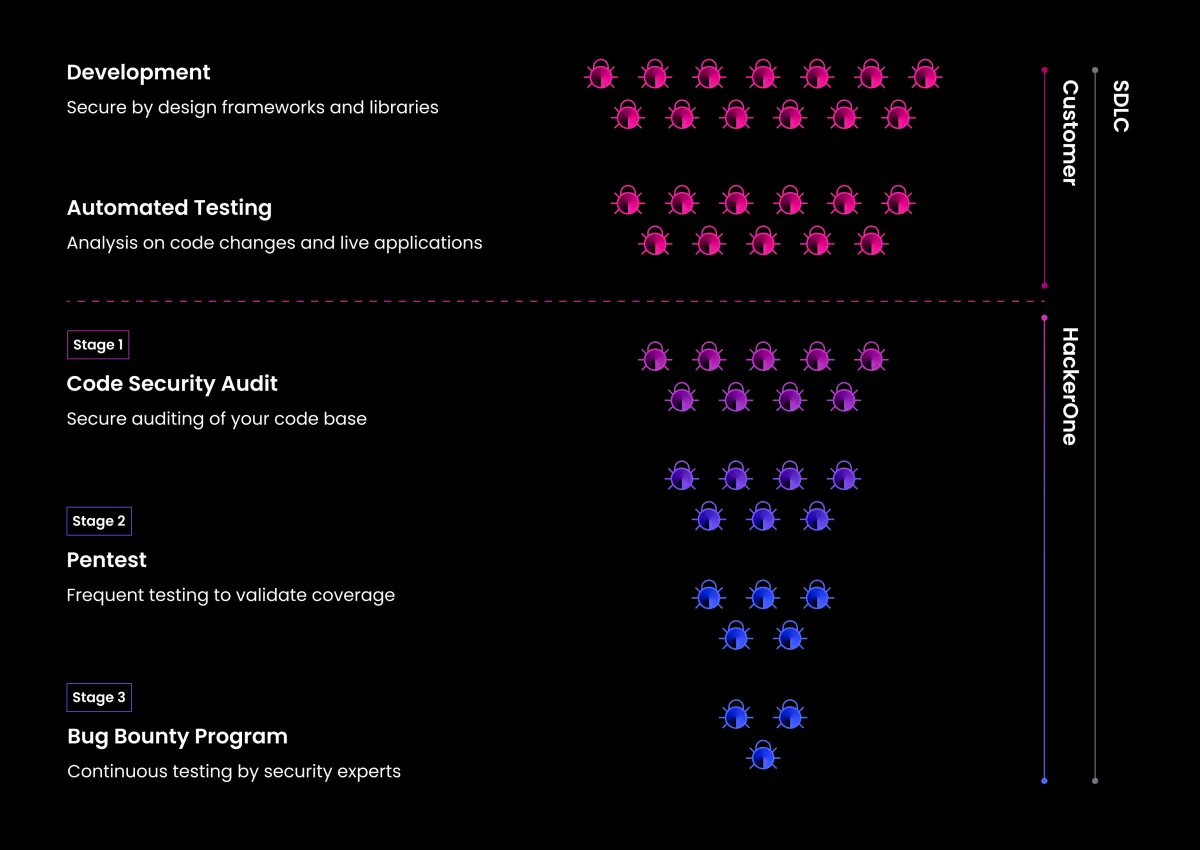
HackerOne helps high-growth companies increase their attack resistance via a 3-stage process

Code Security Audit
Background-checked, skills-vetted engineers scour your source code for security flaws, escalating risks that need attention and providing context-specific guidance for fast resolution.
Three stages of continuous vulnerability discovery
Explore the three key pillars of our Attack Resistance Platform that help you pinpoint the most critical flaws in your asset inventory, prioritise what to fix first, and reduce your threat exposure.
Pentest as a Service
Need a penetration test for SOC 2, ISO 27001, and more? Get started in days, not weeks, and receive test results as they happen—thanks to a legion of ethical hackers.
Bug Bounty Program
Does your continuous SDLC call for continuous, offensive security testing? Our bug bounty programs find risks that conventional tools and overburdened security teams can’t.
Key Benefits
Change is the only constant for fast-growing companies. Get (and stay) ahead of cybercrime with offensive security built for agility.
Add expertise, not headcount
Call on the creativity of 2M ethical hackers. Increase your security testing coverage and available skill sets, even with constrained budgets. Plus, get expert triage
Call on the creativity of 2M ethical hackers. Increase your security testing coverage and available skill sets, even with constrained budgets. Plus, get expert triage
Test as fast as your SDLC
Your continuous SDLC requires continuous, offensive testing for the best ROI and protection at every phase of the software development life cycle.
Your continuous SDLC requires continuous, offensive testing for the best ROI and protection at every phase of the software development life cycle.
Know where your risks lie
Traditional and AI-based testing methods can miss tricky, critical vulnerabilities. Eliminate unknown risks to keep cyber insurance costs down.
Traditional and AI-based testing methods can miss tricky, critical vulnerabilities. Eliminate unknown risks to keep cyber insurance costs down.

f185.webp?itok=9QJ5DUCX)
