Master your vulnerability landscape
Digital transformation is accelerating the expansion of your attack surface, creating more incidents for overburdened security teams to address. Leverage expert insights to strengthen your vulnerability management program.
Continuous watch over your attack surface
Catch what scanners can’t see.
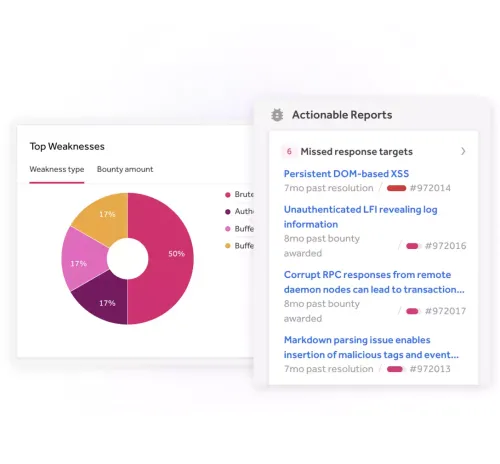
Automated scanning can reveal many vulnerabilities but security experts can detect and triage the critical weaknesses that are most likely to be exploited.
Automated scanning can reveal many vulnerabilities but security experts can detect and triage the critical weaknesses that are most likely to be exploited.
Comply with regulations.
Including vulnerability intelligence and continuous testing from security experts will assure that your organization can meet compliance standards.
Including vulnerability intelligence and continuous testing from security experts will assure that your organization can meet compliance standards.
Less noise, more savings.
Vulnerabilities prioritized by security experts assure that your security operations teams remediate the most critical threats, faster.
Vulnerabilities prioritized by security experts assure that your security operations teams remediate the most critical threats, faster.
Detect risks before they become threats.
With attack vectors spreading across a broad landscape of code, applications, networks and clouds, organizations are looking for innovative ways to harden their security posture.
- Establish a dynamic vulnerability reporting process to receive and manage vulnerability reports from third parties.
- Implement a vulnerability disclosure policy that enhances security operations with vulnerability intelligence from our community of ethical hackers.
- Gain visibility into threats across your assets and effectively measure the risk.
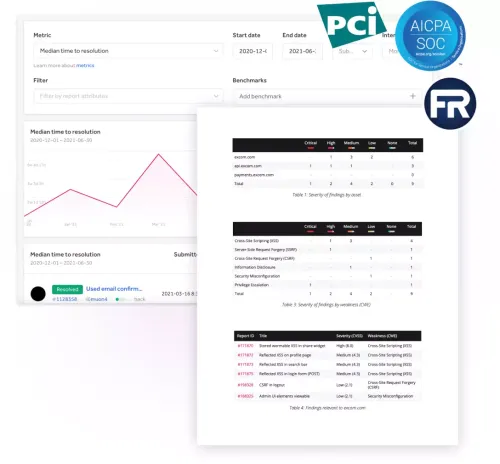
More than compliance. It’s trust.
Organizations across industries must comply with mandates but need input from skilled security experts for maximum risk reduction, without delay.
- Implement security framework to meet compliance and regulatory requirements.
- Stay ahead of the competition with analytics and benchmarking data.
- Build audit or assessment processes to mitigate cyber risk while adhering to evolving regulations.
Find and fix vulnerabilities across critical apps.
Applications are highly diversified, requiring dynamic visibility to pinpoint and fix vulnerabilities. With a continuous security solution powered by a community of ethical hackers, your application ecosystem will be better protected from cyberattacks.
- Ensure security across your entire attack surface with continuous testing and vulnerability intelligence.
- Aggregate vulnerabilities from multiple sources into a single solution for better visibility and prioritization.
- Expose the vulnerabilities caused by shadow IT and significantly minimize your attack surface.