The HackerOne Top 10 Vulnerability Types
HackerOne has been measuring the top ten vulnerabilities reported on our platform for eight years. Despite the investment in security, and industry calls for better security practices earlier in the software development life cycle (SDLC), we see steady increases in vulnerability reports year over year, and most industries are still seeing the most common vulnerabilities reported again and again.
Today's CISO must think about:
Functional leadership
Can we handle and mitigate breaches, incidents and crises?
Can we handle and mitigate breaches, incidents and crises?
Secure generative AI and LLMs
Are we protected in a new era of AI vulnerabilities?
Are we protected in a new era of AI vulnerabilities?
Scaling governance, risk and compliance
Are we meeting regulatory standards?
Are we meeting regulatory standards?
Responsiveness and agility
Are we leveraging information risk to make decisions?
Are we leveraging information risk to make decisions?
The top 10 vulnerabilities need to change.
Valid vulnerabilities on the HackerOne Platform have jumped 12% over the past year, with 78,042 valid issues found across 1,300+ customer programs. While organizations are making efforts to reduce vulnerability reports by identifying trends and putting measures in place to catch them earlier in development, we do expect vulnerability reports to keep rising as more organizations embrace human-led security.
The good news? Reports for the three most common vulnerabilities are all down by a small percentage platform-wide since 2023, with reports for cross-site scripting down 10%, suggesting that some of the tactics to reduce common vulnerabilities are having an impact.
HackerOne data shows that the top ten vulnerabilities reported to customer programs are common and mostly preventable with proactive measures. Catching these issues early in the SDLC can significantly cut down on bounty costs.
Key Takeaways
Researchers and security professionals alike see AI as both a risk and an opportunity. 48% of security leaders said that generative AI (GenAI) was one of the most significant risks they saw impacting their organization, with data integrity being a key priority to secure.
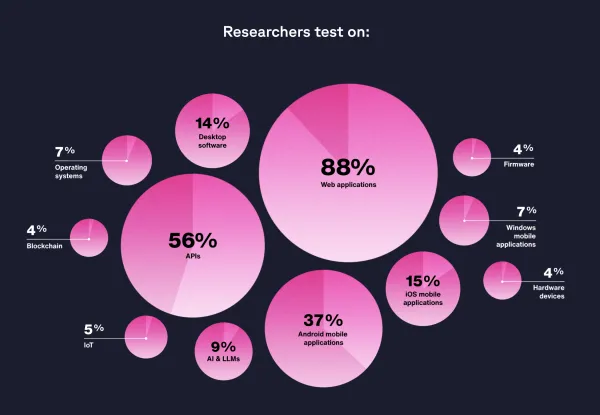
The security researcher community is maturing its skill sets to meet the demands of customers, with more members focusing on mobile, APIs, and AI deployments as testing scope expands to more varied attack surfaces. Nearly 10% of researchers now specialize in AI to meet the growing demand of AI testing engagements.
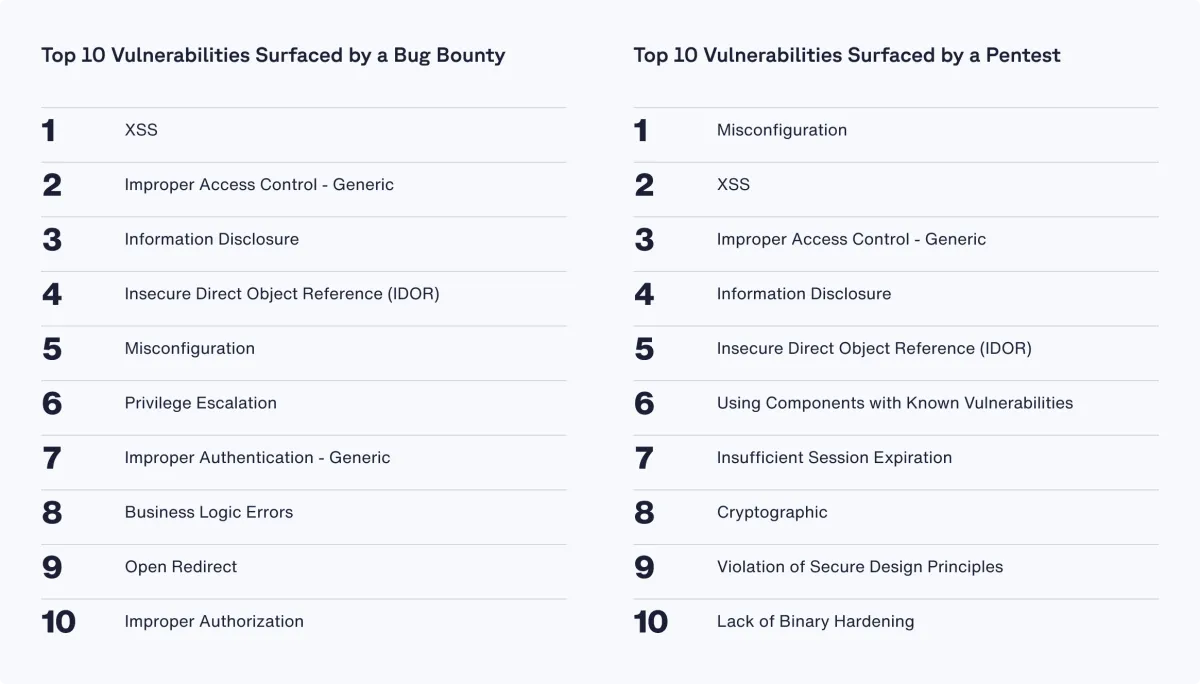
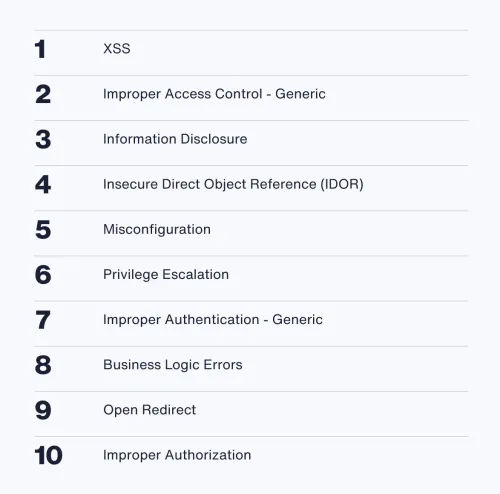
The top vulnerability reported to a bug bounty program is cross-site scripting (XSS), whereas for a pentest it’s misconfiguration. Pentests tend to uncover more systemic or architectural vulnerabilities while security researchers working on bug bounty programs focus more on real-world attack vectors, user-level issues, and business logic flaws.
The most security-resilient organizations have refined their engagement with the researcher community to achieve the ideal formula for impactful results, focusing on a broad scope and a select team of trusted researchers. High-impact programs—those with over 30% of valid vulnerability submissions rated as high or critical—work with fewer researchers; the average number of researchers on a high-impact program is 56, vs. 97 on lower-impact programs.
The most technologically advanced industries are seeing results when it comes to the efforts to reduce common vulnerabilities in production, with Web3 companies seeing 65% fewer reports for cross-site scripting than the industry average.
Bugs Surfaced: Bug Bounty vs. Pentest
Bug bounty
Bug bounty programs focus on real-world attack vectors and user-level issues like business logic flaws, privilege escalation, and open redirects. Pentests, on the other hand, uncover more systemic or architectural vulnerabilities, such as components with known vulnerabilities, cryptographic weaknesses, or secure design violations.
Pentest
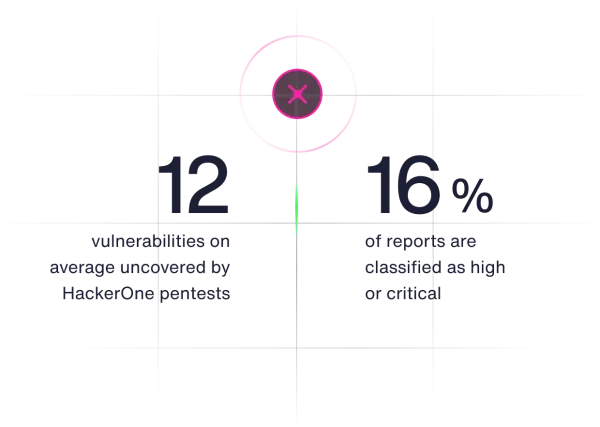
On average, each HackerOne pentest uncovers 12 vulnerabilities, with 16% of reports classified as high or critical. Paired with HackerOne’s bug bounty programs, which report an average of 25% high or critical issues, pentesting provides a robust solution for identifying security gaps and ensuring comprehensive coverage.
Learn more in the Hacker-Powered Security Report
This 8th Annual Hacker-Powered Security Report compiles insights, data, and analysis from customers, security researchers, and HackerOne’s comprehensive vulnerability database. The insights are gathered from:
- Aggregated, anonymized data from the HackerOne Platform, made up of over 500,000 valid vulnerability reports.
- Our annual survey of 2,000+ highly skilled and active members of the security researcher community, covering topics ranging from the time they dedicate to hacking to their views on AI regulations. The respondents reflect the diversity of location, experience, expertise, and age that defines HackerOne’s global community of security researchers.
- Our annual survey of 50 customers, representing a range of organizational sizes, structures, and industries.
- A survey, conducted in partnership with Opinion Matters, of 500 security leaders globally about their approach to cybersecurity challenges.
e996.webp?itok=Z5C1vM9K)